Software development is continuously evolving, and containers have become a real game-changer technology in this field. They are used to build, deploy and manage applications by the devops teams of some of the biggest tech companies in the world.
These lightweight, portable units of software, designed to run anywhere, have become the backbone of modern cloud-native architectures, offering unprecedented flexibility and efficiency. Unlike virtual machines, which emulate entire hardware systems, containers virtualize only the operating system level. This makes them significantly faster and more resource-efficient. To learn more about the differences between containers and virtual machines, check out our blog post on the topic.
However, simply using containers isn’t enough. To truly harness their potential, developers must adhere to a set of industry standard best practices that ensure security, scalability, and optimal performance. This blog post will delve into six essential container best practices that will help you build and manage robust containerized applications.
1. Building containers
Building containers typically involves creating a Dockerfile, a file that specifies the steps to build an image. This includes defining the base image, installing dependencies, and copying application code.
Key tips
- Base image selection: Choose official, minimal base images like Alpine Linux for smaller footprints and prefer images from trusted sources like Docker Hub.
- Minimal Dockerfiles: Write concise Dockerfiles to reduce image size and potential vulnerabilities.
- Multi-stage builds: Use multi-stage builds to create lean production images by discarding unnecessary layers.
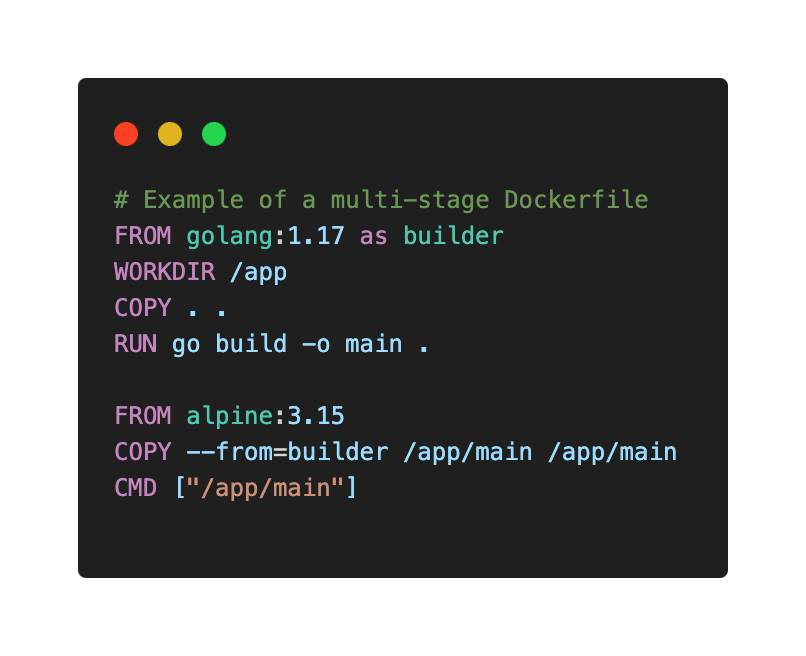
- Image source and updates: Verify the source of base images and keep them updated to address security vulnerabilities.
Security considerations
- Regularly scan images for vulnerabilities using tools like Trivy or Clair.
- Remove package managers and unnecessary tools after installation.
- Run containers as non-root users when possible.
2. Storing containers
Once built, containers need to be stored in a container registry. This allows for easy sharing, versioning, and deployment. Popular options include Docker Hub, GitHub Container Registry, and Amazon ECR.
Key tips
- Private registries: Use private registries for sensitive applications to enhance security. Some common private registries are Amazon ECR, Google Container Registry, Azure Container Registry etc.
- Public registries: Use public registries only from dedicated companies. Some common public registries are Docker Hub, GitHub Container Registry etc.
- Access control: Implement robust access control and authentication mechanisms. Use Role-Based Access Control (RBAC) for granular permissions.
- Registry cleanup: Regularly clean up unused images to optimize storage.
- Image verification: Implement image signing and verification.
3. Tagging containers
Container tagging is far more than a simple naming convention — it’s a critical practice for maintaining traceability, reproducibility, and version control. Tagging containers with semantic versioning helps in tracking changes and managing deployments. Avoid using the “latest” tag in the production environment to ensure consistency.
Key tips
- Immutable tags: Use immutable tags to maintain traceability and reliability.
- Automated tagging: Integrate automated tagging into your CI/CD pipelines.
- Adopt semantic versioning: Use a clear format like v1.0.0 that indicates major, minor, and patch versions.
- Avoid the “latest” tag: In production environments, always use specific version tags to ensure consistency and predictability.
Tagging Workflow Example
Although every organization has its own tagging and versioning practices, the following is a common approach based on Semantic Versioning (SemVer):
- 1.0.0-alpha: Initial development version
- v1.0.0-beta: Pre-release version
- v1.0.0: Stable production release
- v1.1.0: New backwards-compatible features
- v1.1.1: Bug fixes
4. Secrets management
Managing secrets securely is paramount in deploying any application to production. Never hardcode sensitive information like API keys or passwords directly into container images.
Key tips
- CI/CD integration: Integrate secrets management into your CI/CD pipelines.
- Use dedicated Secrets Management Tools: Leverage solutions like HashiCorp Vault and AWS Secrets Manager for managing secrets.
- Encrypt and restrict access: Ensure secrets are encrypted at rest and transit. Implement least-privilege access principles to ensure secrets are accessible only to authorized services.
- Secret lifespan: Use short-lived secrets when possible and rotate them regularly.
5. Running containers
When running containers, adhere to the principle of single-purpose containers. Each container should run a single application or service and should be managed by a proper orchestration platform.
Key tips
- Single-purpose containers: Design each container to run a single application or in a microservice architecture.
- Immutability: Treat containers as disposable and replaceable.
- Continuous monitoring: Implement robust monitoring using tools like Prometheus or Datadog to track container performance.
- Orchestration: Use Kubernetes or other orchestration tools to manage containerized applications. Naviteq offers Kubernetes Management service and a team of experts can help you leverage these tools effectively, ensuring smooth deployment, scaling, and management of your containerized applications.
- Monitoring and alerting: Monitor container performance and resource utilization. Implement alerting policies to proactively handle performance bottlenecks.
- Logging and tracing: Use distributed tracing and implement a comprehensive logging strategy.
- Statelessness: Minimize local state storage and make containers stateless as much as possible.
Common mistakes
Some common mistakes to avoid when running containers:
- Containers as root
Running containers as root grants them excessive privileges thus making them vulnerable to attacks.
Solution: Use non-root users and privilege separation to minimize potential damage. - Neglecting image security scans
Failing to scan container images for vulnerabilities can expose your applications to security risks.
Solution: Regularly scan images using tools like Clair or Trivy and keep them up-to-date with the latest security patches. - Using the “latest” tag in production
Using the “latest” tag can lead to unpredictable deployments and potential instability.
Solution: Employ semantic versioning to tag images and use specific tags in production environments. - Storing state within containers
Storing state within containers can hinder scalability and portability.
Solution: Use persistent storage solutions like volumes or external databases to store stateful data. - Overlooking resource constraints
Not setting appropriate resource limits and requests can lead to resource contention and performance degradation.
Solution: Define clear resource limits and requests to ensure optimal resource allocation. - Ignoring logging and monitoring
Lack of proper logging and monitoring can make it difficult to troubleshoot issues and identify performance bottlenecks.
Solution: Implement robust logging and monitoring solutions to track container health and performance.
6. Stateless containers
Design your applications to be stateless, meaning they don’t store data locally. This enhances portability and scalability.
Key tips
- Ephemeral containers: Make containers easily disposable and replaceable.
- Leverage persistent volumes: In Kubernetes, use Persistent Volumes for managing external storage of stateful applications.
- External storage: Use external storage solutions like Amazon S3, Google Cloud Storage, Azure Blob Storage, Network File Systems (NFS) etc.
Real-world example of stateless containers
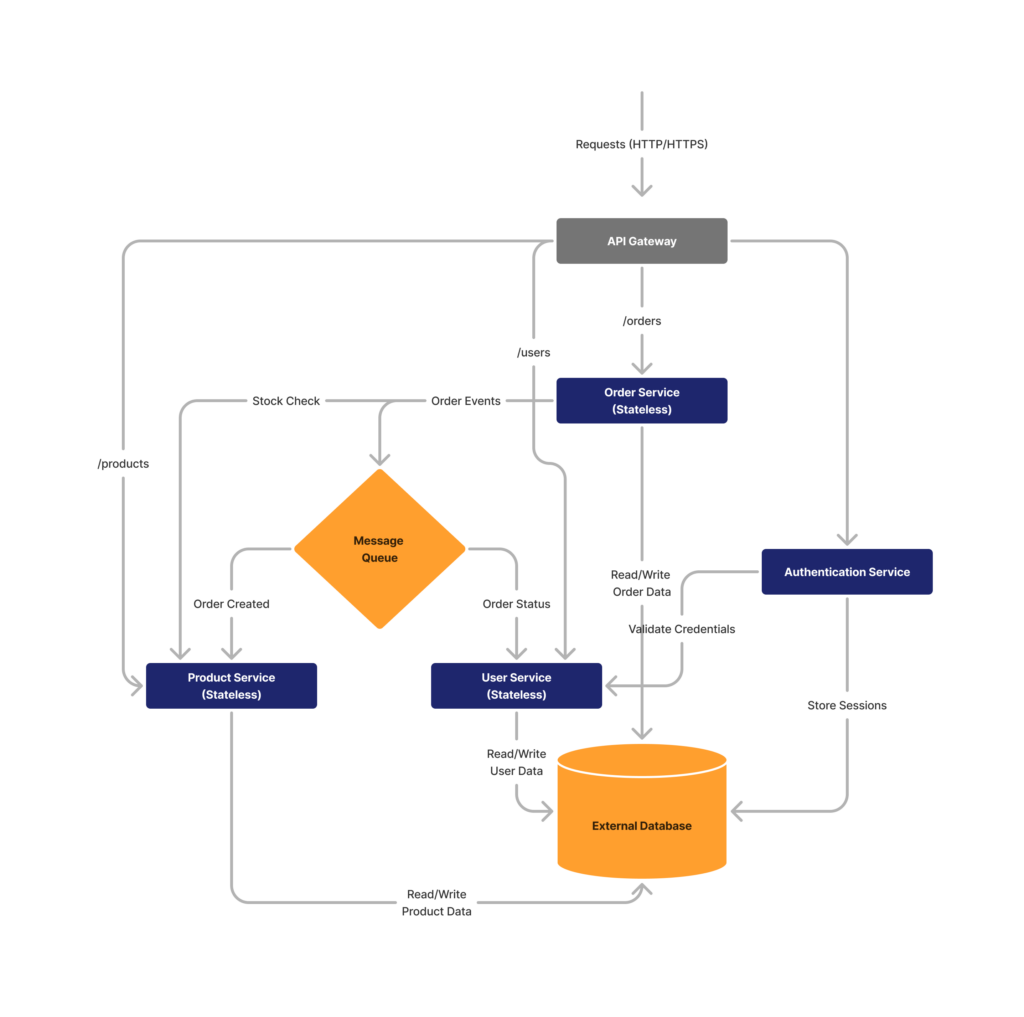
A real-world industry-standard example of stateless containers being used by an e-commerce company is explained below. This approach breaks down a traditional monolithic application into smaller, independent services that are highly scalable. Each service can be containerized, making it easier to deploy, scale, and manage.
Key architectural components
- API gateway
◦ Acts as the single entry point for all client requests.
◦ Handles routing, load balancing, and request authentication.
◦ Provides a unified interface for different microservices. - Product service
◦ Manages product-related operations.
◦ Handles product catalog, inventory management.
◦ Provides endpoints for product search, details, and pricing. - Order service
◦ Manages the entire order lifecycle.
◦ Handles order creation, processing, and tracking.
◦ Integrates with payment and inventory systems. - User service
◦ Manages user-related functionalities.
◦ Manages user profiles and preferences.
◦ Acts as a front for other critical services like Authentication Service. - External database
◦ SQL databases such as MySQL/PostgreSQL or NoSQL databases such as MongoDB/Amazon DynamoDB can be used as per the requirements of the project.
◦ Provides persistent data storage.
◦ Supports multiple services with scalable and distributed database solutions. - Message queue
◦ Enables asynchronous communication between services.
◦ Supports event-driven architectures.
◦ Ensures reliable message delivery and system resilience.
◦ Some common message queue options are RabbitMQ and Amazon SQS
Scalability and performance considerations
- Each microservice can be independently scaled.
- Kubernetes can implement automatic scaling strategies. It can adjust application resources in response to load fluctuations, leveraging both native and third-party tools.
- Supports elastic infrastructure and cost optimization.
Performance optimization
- Implement caching layers (Redis)
- Use content delivery networks (CDNs)
- Optimize database queries
- Implement efficient load balancing
Security implementations
- Run containers with minimal privileges.
- Use dedicated secrets management.
- Implement network policies.
- Regular vulnerability scanning.
Monitoring and observability
- Prometheus for metrics collection.
- Grafana for visualization.
- ELK Stack (Elasticsearch, Logstash, Kibana), Loki or VictoriaLogs for logging.
- Distributed tracing with Jaeger.
Containerized e-commerce architecture offers unprecedented flexibility, scalability, and performance. By breaking down monolithic applications into microservices, organizations can:
- Improve system resilience.
- Enable faster deployments.
- Support continuous innovation.
- Optimize resource utilization.
The key is thoughtful design, robust implementation, and continuous improvement. Naviteq’s DevOps as a Service can help you navigate the complexities of containerized architectures. Our team of experts can assist with designing and implementing a DevOps containerization strategy tailored to your specific needs, provisioning and configuring the necessary infrastructure for containerized deployments, setting up automated CI/CD pipelines for efficient and reliable deployments, implementing robust monitoring and logging solutions to track application health and performance, and ensuring the security of your containerized applications through best practices and security tools. In case you are currently using virtual machines, you can reference our detailed step-by-step guide for migration from virtual machines to containers.
Conclusion
The following is a quick recap of the above best practices:
- Building containers: Build lean, efficient, and secure containers. Use a minimal base image and only include necessary dependencies. This reduces the image size, improves build times, and minimizes attack surfaces.
- Storing containers: Store container images in a secure and accessible container registry. This centralizes image management, enables version control, and facilitates efficient deployment across environments.
- Tagging containers: Tag images with meaningful and versioned tags to track changes and facilitate deployment. Use clear and consistent naming conventions to identify images easily. Use semantic versioning.
- Secrets management: Employ robust secret management practices to protect sensitive information. Store secrets securely outside of containers and use environment variables or configuration files to inject them during deployment. Use dedicated secrets management tools.
- Running containers: Utilize container orchestration tools like Kubernetes to manage and scale containers effectively. Automate deployment, scaling, and lifecycle management to improve efficiency and reliability.
- Stateless containers: Design containers to be stateless, meaning they don’t store data locally. This enables easy scaling, replication, and recovery. Store persistent data in external storage solutions like databases or object storage.
By implementing these six container best practices, you’ll create secure, scalable, and efficient containerized applications. By prioritizing lean image building, secure storage, effective tagging, robust secret management, efficient orchestration, and stateless design, you can ensure that your applications are reliable, scalable, and maintainable. Approach the process by starting small and iterating continuously. It’s often a wise decision to take the help of industry experts with years of experience in this field like that from Naviteq.
Additional resources
The following are some blog posts and articles related to this topic topic:
- https://aws.amazon.com/blogs/containers/category/post-types/best-practices/
- https://cloud.google.com/blog/products/containers-kubernetes/7-best-practices-for-building-containers
- https://www.naviteq.io/blog/how-to-scale-kubernetes-nodes-on-the-aws-eks/
Ready to get started?
Contact Naviteq today to learn how our experts can help you containerize your applications in an efficient and scalable manner.
Back to blog


